Network Fundamentals
- VPN: Virtual Private Network
o A method of encrypting point to point a cross a public network
- VOIP: Voice over Internet Protocol
o Delivery of voice communication over IP network
o service converts your voice into a digital signal that travels over the internet
- SAM: Security Account Manager
o Database that contain user account and security descriptors in work group
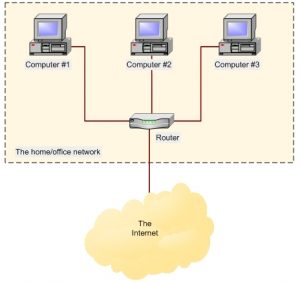
- LAN: Local Area Network
o Linking two or more pc and related devices within a limited area
- MAN: Metropolitan Area Network
o Larger than LAN and smaller than WAN
- WAN: Wide Area Network
o Used to connect LANs together
- MAC: Media access Control
o Responsible for hardware addressing
- The Domain Name:
o It’s just the website name for ex: www.WE.net called Domain name.
- The Name Server:
o It’s the server which contains the Zone files for the customer’s domain that includes the important information of the domain like (A & MX records).
- The Hosting Server:
o It’s the server which contains the FTP files of the customer domain and it can be shared or detected.
- The mail server:
o It’s the server which the customer should has if he wants to create E-mails under his domain for ex. ([email protected])
- HTML: Hypertext Markup Language
o Is the simplest code for creating web pages all servers whatever the site made with sends data to browser via html format
- NAT: network address translation
o Is the translation of an Internet Protocol address (IP address) used within one network to a different IP address known within another network, One network is designated the inside network and the other is the outside. Typically, a company maps it’s local inside network addresses to one or more global outside IP addresses and unmaps the global IP addresses on incoming packets back into local IP addresses. This helps ensure security since each outgoing or incoming request must go through a translation process that also offers the opportunity to qualify or authenticate the request or match it to a previous request. NAT also conserves on the number of global IP addresses that a company needs and it lets the company use a single IP address in its communication with the world.
- Difference between half duplex and full duplex
o Duplex
- The way modems exchange data: half duplex or full duplex. With half duplex transmissions, only one modem can send data at a time. Full duplex transmissions allow both modems to send data simultaneously.
o Half duplex
- Mode enables networking devices to send data one-way at a time, means both networking devices cannot send data at the same time. It’s like walkie-talkie, only one person can talk at a time.
o Full duplex
- It enables two networking devices to send data at the same time and it improves network performance. It’s like making a call to your friend by using telephone or cell phone, both of you can talk and listen at the same time.
- Difference between analog and digital signals.
o Analog signals
- Use continuously variable electric currents and voltages to reproduce data being transmitted. Since data is sent using variable currents in an analog system, it is very difficult to remove noise and wave distortions during the transmission. For this reason, analog signals cannot perform high-quality data transmission.
o Digital signals
- Use binary data strings (0 and 1) to reproduce data being transmitted. Noise and distortions have little effect, making high-quality data transmission possible. INS-Net’s high-quality digital data transmission at high speeds is especially beneficial for transmission using computers since computers themselves utilize digital signals for information processing.
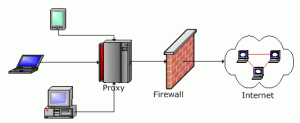
- Difference between Firewalls & Proxy
o Firewall
- A part of a computer systemor network that protects the system by preventing unauthorized access over the internet. A proxy server is one type of firewall.
o Basic Firewall Function
- A firewall works by examining each packet of information sent between the protected computer and computersoutside the local network. Packets that do not meet certain rules are blocked.
o Other Types of Firewall
- Most firewalls are software programs instead of separate computers like a proxy server. The program monitors the internet traffic of a computer and allows or denies access based on rules set by a user.
o Proxy Server
- A proxy server is a computer that sits between a local network and the rest of the internet. All outside access to the network must pass through this server.
o Proxy Advantages
- Because all traffic to protected computers must pass through the proxy server, outside users cannot uncover the specific network addresses of computers in the local network, which adds an additional layer of security.
o Proxy Disadvantages
- The owner of the proxy server can see all the traffic between the network and the outside internet, which could limit the privacy of individual users inside the proxy. Also, proxy servers require a large setup and thus are not practical for single computers.
- Signal-to-noise ratio
o (Often abbreviated SNR or S/N) is a measure to quantify how much a signal has been corrupted by noise. It is defined as the ratio of signal power to the noise power corrupting the signal.
o The ratio is usually measured in decibels (dB).
o What is: SNR Margin and Line Attenuation? .Does it helps to know my line quality?
o SNR
SNR means Signal to Noise Ratio. Simply put divide the Signal value by Noise Value and you get SNR. You need high SNR for a stable connection. In general, a higher signal to noise ratio will result in less errors.
•6bB. or below = Bad and will experience no line synchronization and frequent disconnections
•7dB-10dB. = Fair but does not leave much room for variances in conditions.
•11dB-20dB. = Good with little or no disconnection problems
•20dB-28dB. = Excellent
•29dB. or above = Outstanding
Note that most modems display value as SNR Margin and not pure SNR.
o SNR Margin
you can think of SNR margin as the measure of quality of the service; it defines the ability of the service to work error free during noise bursts.
This is a measure of the difference between your current SNR and the SNR that is required to keep a reliable service at your connection speed. If your SNR is very close to the minimum required SNR, you are more likely to suffer intermittent connection faults, or slowdowns. You need a high margin to ensure that bursts of interference don’t cause constant disconnections.
With traditional broadband, the higher the SNR Margin, the better. With MaxDSL the faster speeds are only available as a trade-off with what your line can reliably support. The Target SNR Margin is about 6dB. If your broadband is provided through an LLU (Local Loop Unbundled) network, this target SNR Margin may be as high as 12dB.
- Line Attenuation
o In general, attenuation is the loss of signal over distance. Unfortunately, dB loss is not just dependent on distance. It also depends on cable type and gauge (which can differ over the length of the cable), the number and location other connection points on the cable.
o 20bB. And below = Outstanding
o 20dB-30dB. = Excellent
o 30dB-40dB. = Very Good
o 40dB-50dB. = Good
o 50dB-60dB. = Poor and may experience connectivity issues
o 60dB. And above = Bad and will experience connectivity issues
o Line attenuation also affects your speed.
o 75 dB+: Out of range for broadband
o 60-75 dB: max speed up to 512kbps
o 43-60dB: max speed up to 1Mbps
o 0-42dB: speed up to 2Mbps+
o Assuming that your SNR is low, you can do the following to increase your SNR are the following:
- Identify where the telephone wire runs into your home
- Trace it all the way back to the junction box
- Check whether the cable is in good shape – not too much weathered, no welds , the wire doesn’t pass by any electrical wires or satellite cables etc.
- At the junction box, check the connection. Is it corroded, oxidized? If yes, note it down.
- Difference between RJ11 & RJ45
o RJ
- A registered jack is a standardized physical network interface— both jack construction and wiring pattern — for connecting telecommunications or data equipment to a service provided by a local exchange carrier or long distance carrier.
o RJ11
- A common jack type most often used for connecting analogue phones, modems and fax machines to a communications line.
o RJ45
- Is a standard type of connector for network cables. RJ45 connectors are most commonly seen with Ethernetcables and networks.
- RJ45 connectors feature eight pins to which the wire strands of a cable interface electrically. Standard RJ-45 pinouts define the arrangement of the individual wires needed when attaching connectors to a cable.
- Ethernet Cable – Color Coding Diagram
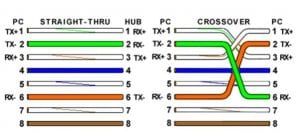
o Simple pin-out diagrams of the two types of UTP Ethernet cables and watch how committees can make a can of worms out of them. Here are the diagrams:
o Note that the TX (transmitter) pins are connected to corresponding RX (receiver) pins, plus to plus and minus to minus. And that you must use a crossover cable to connect units with identical interfaces. If you use a straight-through cable, one of the two units must, in effect, perform the cross-over function.
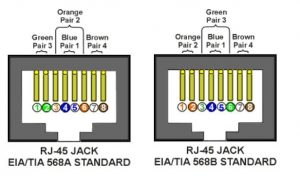
o Two wires color-code standards apply: EIA/TIA 568A and EIA/TIA 568B. The codes are commonly depicted with RJ-45 jacks as follows (the view is from the front of the jacks):
o If we apply the 568A color code and show all eight wires, our pin-out looks like this:
o Note that pins 4, 5, 7, and 8 and the blue and brown pairs are not used in either standard. Quite contrary to what you may read elsewhere, these pins and wires are not used or required to implement 100BASE-TX duplexing–they are just plain wasted.
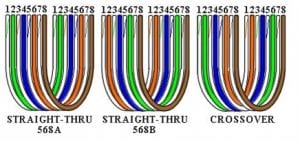
o However, the actual cables are not physically that simple. In the diagrams, the orange pair of wires is not adjacent. The blue pair is upside-down. The right ends match RJ-45 jacks and the left ends do not. If, for example, we invert the left side of the 568A “straight”-thru cable to match a 568A jack–put one 180° twist in the entire cable from end-to-end–and twist together and rearrange the appropriate pairs, we get the following can-of-worms:
o This further emphasizes, I hope, the importance of the word “twist” in making network cables which will work. You cannot use a flat-untwisted telephone cable for a network cable. Furthermore, you must use a pair of twisted wires to connect a set of transmitter pins to their corresponding receiver pins. You cannot use a wire from one pair and another wire from a different pair.
o Keeping the above principles in mind, we can simplify the diagram for a 568A straight-thru cable by untwisting the wires, except the 180° twist in the entire cable, and bending the ends upward. Likewise, if we exchange the green and orange pairs in the 568A diagram we will get a simplified diagram for a 568B straight-thru cable. If we cross the green and orange pairs in the 568A diagram we will arrive at a simplified diagram for a crossover cable. All three are shown below.
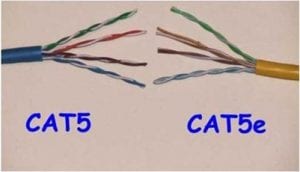
o Transmission speed for Cat 5, Cat 5e, Cat 6 network cable
Cat 5 and Cat 5e UTP cables can support 10/100/1000 Mbps Ethernet. Although Cat 5 cable may support to some degree in Gigabit Ethernet (1000 Mbps), it performs below standard during high-data transfer scenarios.
o Cat 6 UTP cable is manufactured targeting on Gigabit Ethernet and backward compatible with 10/100 Mbps Ethernet. It performs better then Cat 5 cable with higher transmission rate and lower transmission error. If you plan to have Gigabit network, look for Cat 5e or Cat 6 UTP cables.
o Protocols:
- The protocol defines a common set of rules and signals that computers on the network use to communicate.
- TCP/IP model, or internet protocol suite
- Describes a set of general design guidelines and implementation of specific networking protocols to enable computers to communicate over a network
- TCP/IP provides end to end connectivity specifying how data should be addressed, transmitted, routed and received at the destination
- TCP: transmission control protocol
- Provide reliable delivery of data
- UDP: user datagram protocol
- Allows datagram to be exchanged without acknowledgement
- IP: Internet Protocol
o IP is an address of a computer or other network device on a network using IP or TCP/IP. For example, the number “166.70.10.23” is an example of such an address. These addresses are similar to addresses used on houses and help data reach its appropriate destination on a network.
There are several IP addresses used or automatically assigned on a network. For example:
166.70.10.0 0 is the automatically assigned network address.
166.70.10.1 1 is the commonly used address used as the gateway.
166.70.10.2 2 is also a commonly used address used for a gateway.
166.70.10.255 255 is automatically assigned on most networks as the broadcast address
- DHCP: Dynamic host configuration protocol
- Port number
– DHCP client 546 /TCP UDP
– DHCP server 546 /TCP UDP
- Allows a server to dynamically distribute IP addressing and there is a lot of information a DHCP server can provide to a host when the host is requesting an IP address from the DHCP server such as IP address , subnet mask, default gateway, DNS, domain name , WINS information.
- DNS: domain name service (server)
o Resource locator
o Resolves host name to IPs and other wise
o Resolve a fully qualified domain name (FQDN)
o Consists of:
- A record: resolve domain name to IP address
- MX record: resolve mail server to IP address
- PTR record: opposite the A record and MX record, Resolve IP address to domain name or mail server
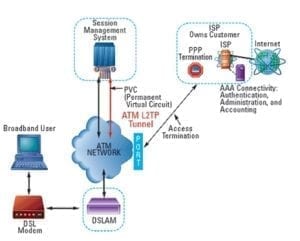
- PPP: Point to Point Protocol
o A protocol that allows a computer to connect to the Internet through a dial-in connection and enjoy most of the benefits of a direct connection; including the ability to run graphical front ends such as Internet Browsers. PPP is generally considered superior to SLIP, because it features error detection, data compression, and other elements of modern communications protocols that SLIP lacks.
- PPPOE: Point to point protocol over Ethernet
o A network protocol for encapsulating point to point protocol (PPP) frame inside Ethernet frames.
o It is used mainly with DSL services where individual users plain metro Ethernet networks.
- SMTP: simple mail transfer protocol
o Port number 25 /TCP UDP
o Is user to send mail (outgoing)
- POP3: post office protocol
o Port number 110 /TCP
o Is used to receive mail (incoming)
- FTP: file transfer protocol
o Port number 21 /TCP
o Let’s us transfer files and it can make this between any two machine
o FTP is not just a protocol, it’s also a program
o Such as: perform file task by hand
o Allows for access to both directories & files
o It’s secure so users must be subjected to an authentication login (secured with user name and password implemented by system administrators to restrict access)
o FTP is an option you should consider if you are in need of sending and receiving large files (because most ISPs don’t allow files larger than 5 MB to be emailed)
o FTP is faster than e-mail, which is another reason to use ftp for sending or receiving large files
- SNMP: simple network management protocol
o Port number 161 /UDP
o Collect and manipulates valuable network information
o Or it used to manage TCP/IP-based and IPX-based networks.
- HTTP: hypertext transfer protocol
o Port number 80 /TCP
o Application level protocol, it’s used for returning interlinked resources called hyper text documents to the establishment of the World Wide Web
o HTTP /1.0 used a separate connection for every document
o HTTP /1.1 can reuse the same connection to download.
- LDAP: lightweight directory access protocol
o Port number 389 /TCP
o Is a protocol for clients to query and manage information in a directory service over TCP connection port 389
- OSPF: open shortest path first
o Consists of areas and autonomous systems
o Minimizes routing update traffic
o Allows scalability
o Has unlimited hop count
o Allows multi-vendor deployment (open standard)
o Support VLSM
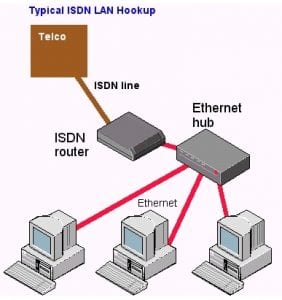
- ISDN: Integrated services digital network
o An international communications standard for sending voice, video, and data over digital telephone lines or normal telephone wires. ISDN supports data transfer rates of 64 Kbps (64,000 bits per second).
o There are two types of ISDN:
o Basic Rate Interface (BRI) — consists of two 64-Kbps B-channels and one D-channel for transmitting control information.
o Primary Rate Interface (PRI) — consists of 23 B-channels and one D-channel (U.S.) or 30 B-channels and one D-channel (Europe).
o The original version of ISDN employs baseband transmission. Another version, called B-ISDN, uses broadband transmission and is able to support transmission rates of 1.5 Mbps. B-ISDN requires fiber optic cables and is not widely available.
- Leased line
o Is a telephone line that has been leased for private use, In some contexts, it’s called a dedicated line. A leased line is usually contrasted with a switched line or dial-up line.
o Typically, large companies rent leased lines from the telephone message carriers (such as AT&T) to interconnect different geographic locations in their company. The alternative is to buy and maintain their own private lines or, increasingly perhaps, to use the public switched lines with secure message protocols. (This is called tunneling).
- Local loop
- In telephony, a local loop is the wired connection from a telephone company’s central officein a locality to its customers’ telephones at homes and businesses. This connection is usually on a pair of copper wires called twisted pair. The system was originally designed for voice transmission only using analog transmission technology on a single voice channel. Today, your computer’s modem makes the conversion between analog signals and digital signals. With Integrated Services Digital Network (ISDN) or Digital Subscriber Line (DSL), the local loop can carry digital signals directly and at a much higher bandwidth than they do for voice only.
- Spyware
o Is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge? The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user’s personal computer. Sometimes, however, spywares such askey loggers are installed by the owner of a shared, corporate, or public computer on purpose in order to secretly monitor other users.
o While the term spyware suggests software that secretly monitors the user’s computing, the functions of spyware extend well beyond simple monitoring. Spyware programs can collect various types of personal information, such as Internet surfing habits and sites that have been visited, but can also interfere with user control of the computer in other ways, such as installing additional software and redirecting Web browser activity. Spyware is known to change computer settings, resulting in slow connection speeds, different home pages, and/or loss of Internet connection or functionality of other programs. In an attempt to increase the understanding of spyware, a more formal classification of its included software types is provided by the term privacy-invasive software.
o In response to the emergence of spyware, a small industry has sprung up dealing in anti-spyware software. Running anti-spyware software has become a widely recognized element of computer security practices for computers, especially those running Microsoft Windows. A number of jurisdictions have passed anti-spyware laws, which usually target any software that is surreptitiously installed to control a user’s computer.
o Universal Serial Bus (USB)
o Universal Serial Bus (USB) is a set of connectivity specifications developed by Intel in collaboration with industry leaders. USB allows high-speed, easy connection of peripherals to a PC. When plugged in, everything configures automatically. USB is the most successful interconnect in the history of personal computing and has migrated into consumer electronics (CE) and mobile products.
o Important Notes
- The upload speed in the above table is calculated by Kilobyte (8 bit =1 byte).
- The download speed in the above table is calculated by Kilobyte (KB).
- Network Devices
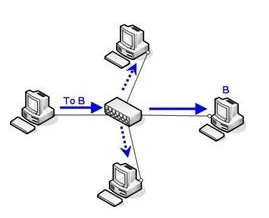
- Hub
o The least intelligent kind of networking device.
o Operate at physical layer (layer 1).
o Takes data in one port and then transmits it out every other port, so any information send or received by any single PC on a Hub is transmitted to every other PC, this is bad for security.
o Uses up a lot of band width on the network, as computers have to receive data that they don’t need.
- Switch (Bridge)
o More intelligent kind of networking device.
o Multi-Port Bridge operates at data link layer (layer 2).
o Know MAC address of each PC, so when data comes into the Switch it only send data back out the port assigned to the computer’s MAC address.
o Join multiple computers together within one local area network (LAN) or the same network.
o Switch conserves network Band width and generally better performance than Hub.
- Router
o The most intelligent kind of networking device.
o Operate at network layer (layer 3).
o Router can read IP address of each PC and each network, so router can take internal traffic band for destination out on the internet and route it from your internal network to the external network.
o Join multiple wired or wireless networks together, meaning that connects networks as Gate way do.
- Repeaters
o The repeater is equipment which makes it possible to exceed the maximum length imposed by the standard of a network. To be done it amplifies and regenerates the electric signal.
o It is also able to insulate a failing section (open Cable for example) and to adapt two different Ethernet media. (For example 10base2 towards 10BaseT). This last use which is currently the principal one.
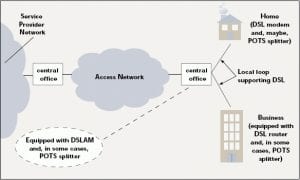
- DSLAM: Digital Subscriber Line Access Multiplexer
o It is a network device, located in the telephone exchange of the service providers
o Connects multiple customer digital subscriber lines (DSLs) to a Single – High – Speed Internet back bone line by using multiplexing techniques.
o In terms of the OSI – Layer Model, the DSLAM acts like a massive network switch, so it’s functionality in layer 2, so it’s cannot re-route traffic between multiple IP networks.
- Modem
o Modulator/Demodulator: a modem transforms (modulates) digital information into an analogue signal that can be sent across a telephone line. It also demodulates an analogue signal it receives from the telephone line, converting the information contained in the signal back into digital information.
- PSTN (public switched telephone network)
o Is the world’s collection of interconnected voice-oriented public telephone networks, both commercial and government-owned, it’s also referred to as the Plain Old Telephone Service (POTS). It’s the aggregation of circuit-switching telephone networks that has evolved from the days of Alexander Graham Bell (“Doctor Watson, come here!”). Today, it is almost entirely digital in technology except for the final link from the central (local) telephone office to the user.
o In relation to the Internet, the PSTN actually furnishes much of the Internet’s long-distance infrastructure. Because Internet service providers ISPs pay the long-distance providers for access to their infrastructure and share the circuits among many users through packet-switching, Internet users avoid having to pay usage tolls to anyone other than their ISPs.
- Broadband Internet access
o Often shortened to just “broadband”, is a high data rate connection to the internet – typically contrasted with access using a 56k modem.
o Broadband is often called “high-speed” access to the Internet, because it usually has a high rate of data transmission. In general, any connection to the customer of 256 Kbit/s (0.25 Mbit/s) or greater is more concisely considered broadband Internet access.
- DSL Concept
- DSL: digital subscriber line
o Is a high-speed Internet service like cable Internet, DSL provides high-speed networking over ordinary phone lines using broadband technology, DSL technology allows Internet and telephone service to work over the same phone line without requiring customers to disconnect either their voice or Internet connections.
o There are basically two types of DSL techniques
o Asymmetric: ADSL, RADSL, VDSL
o Symmetric: SDSL, HDSL, SHDSL
- ADSL: asymmetric digital subscriber line
o It provides higher bit rates in the downstream direction than the upstream direction
o ADSL divides the bandwidth of the twisted-pair cable (one MHZ) into 3 bands
o 1st band between 0 – 25 KHZ is used for regular telephone service that use (4 KHZ) and the rest is used as the guard band to separate the voice channel from the data channel
o 2nd band 25 – 200 KHZ
o Is used for upstream communication
o 3rd band 200 – 1000 KHZ is used for downstream communication
- RADSL: rate adaptive asymmetrical digital subscriber line
o Is a technology based on ADSL, it’s allow different data rates depending on the type of communication voice , data , multimedia and so on
- HDSL: high bit rate DSL
o HDSL uses 2 BIQ encoding which is less susceptible to attenuation
o Data rate is 2 Mbps can be achieved without repeaters and up to a distance of 3.6 Km
o HDSL uses two twisted-pair wires to achieve full-duplex transmission.
- SDSL: symmetric DSL
o Is the same as HDSL but uses one single twisted- pair cable
o SDSL uses echo cancellation to create a full-duplex transmission
- VDSL: very high bit rate DSL
o Similar to ADSL
o Used coaxial, optical fiber or twisted pair cable for short distance (300m -1800m)
o The modulation technique is DMT with a bit rate of 50 – 55 Mbps for downstream and 1.55 – 2.5 Mbps for upstream
o Configuration Parameters
- VPI and VCI: Virtual Path Identifier & Virtual Channel Identifier
o Is used to identify the next destination of cell as it passes through a series of ATM switches on its way to its way to its destination
- PPPOE: Point to point protocol over Ethernet
o Is a network protocol for encapsulating point to point protocol (PPP) frame inside Ethernet Frames
o It is used mainly with DSL services where individual users plain metro Ethernet networks
- MTU: Maximum Transmission Unit
o In computer networking, the term Maximum Transmission Unit (MTU) refers to the size (in bytes) of the largest PDU that a given layer of a communications protocol can pass onwards. MTU parameters usually appear in association with a communications interface (NIC, serial port, etc.). The MTU may be fixed by standards (as is the case with Ethernet) or decided at connect time (as is usually the case with point-to-point serial links). A higher MTU brings greater efficiency because each packet carries more user data while protocol overheads, such as headers or underlying per-packet delays remain fixed, and higher efficiency means a slight improvement in bulk protocol throughput. However, large packets can occupy a slow link for some time, causing greater delays to following packets and increasing lag and minimum latency. For example, a 1500 byte packet, the largest allowed by Ethernet at the network layer (and hence most of the Internet), would tie up a 14.4k modem for about one second.
- LLC: Logical Link Control
o The Logical Link Control (LLC) data communication protocol layer is the upper sub layer of the Data Link Layer specified in the seven-layer OSI model (layer 2). It provides multiplexing and flow control mechanisms that make it possible for several network protocols (IP, IPX) to coexist within a multipoint network and to be transported over the same network media.
The LLC sub-layer acts as an interface between the Media Access Control (MAC) sub layer and the network layer. It is the same for the various physical media (such as Ethernet, token ring, and WLAN).